Locally-configured detectors
Adding a Detector configuration
Locally-configured detectors are configured in your
config.yaml file under the
detectors field.
Example config
concurrency: "8"
detectors:
- keywords:
- keyword1
- keyword2
name: custom regex detector
regex:
id: id-[a-zA-Z0-9]{16}
secret: '[a-zA-Z0-9]{32}'
verify:
- endpoint: http://localhost:8000
headers:
- 'Authorization: Bearer token'
unsafe: true
filterUnverified: true
logLevel: info
numWorkers: 16
trufflehogAddress: https://gnarly-flying-pancake.c1.prod.trufflehog.org
trufflehogScannerGroup: account 1 - us-west-2
trufflehogScannerToken: thog-agent-XXXXXXXXXXXXXXXXXXXXXXXXXX
Custom Regex
Beta detector
The custom regex detector allows you to define your own detector using regular expressions with optional verification using a webhook.
detectors:
- keywords:
- hog
name: hog detector
regex:
adjective: hogs are (\S+)
verify:
- endpoint: http://localhost:8000/
headers:
- 'Authorization: Bearer token'
unsafe: true
keywords are fixed string literals that appear around
or in the regular expression you would like to use. They are required and allow
us to apply the regular expression to only relevant chunks of data, speeding up
scan time. If any one of the provided keywords are found in a chunk of data, the
detector will search for the regular expressions.
The regex section is where you’ll define one or more
named regular expression. A match is one of each of the named regular
expressions. The total number of matches is the Cartesian product of the
regular expressions up to a maximum of 100. For example, if
RegexA has 2 matches: A, B
and RegexB has 3 matches: 1, 2, 3, the total number of matches will be 6: (A, 1), (A, 2), (A, 3), (B, 1), (B, 2), (B, 3).
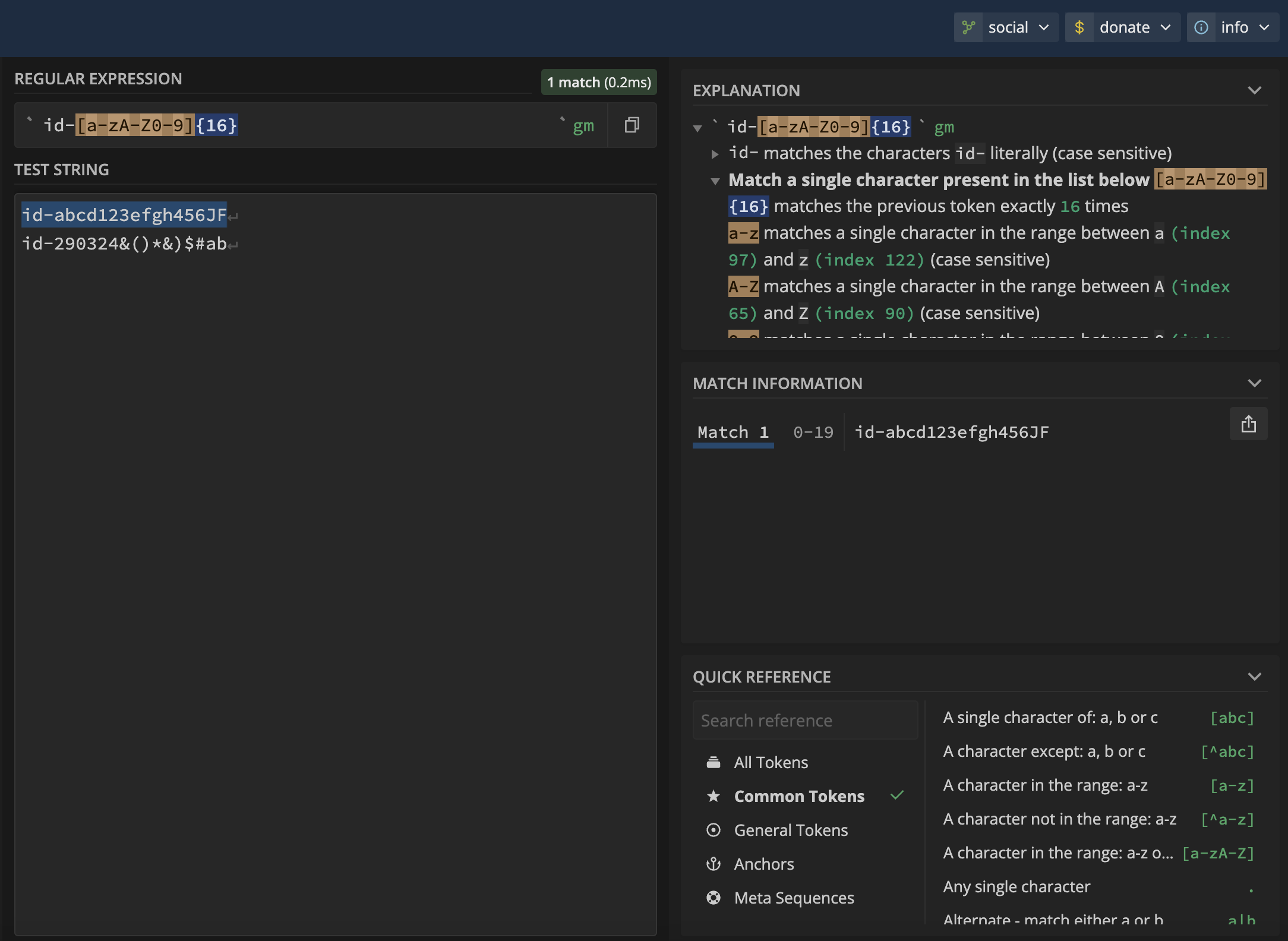
In the above example, the regex section defines regex pattern for id
as a string prepended with id- then followed by a 16 characters comprising
of lowercase and uppercase letters a-z and digits 0-9.
We highly recommend that you test your regex pattern with a site like https://regex101.com/ to ensure that your Custom Detector works as intended.
Testing Regex Patterns
Here’s an example of how to test your regex pattern with Regex101:
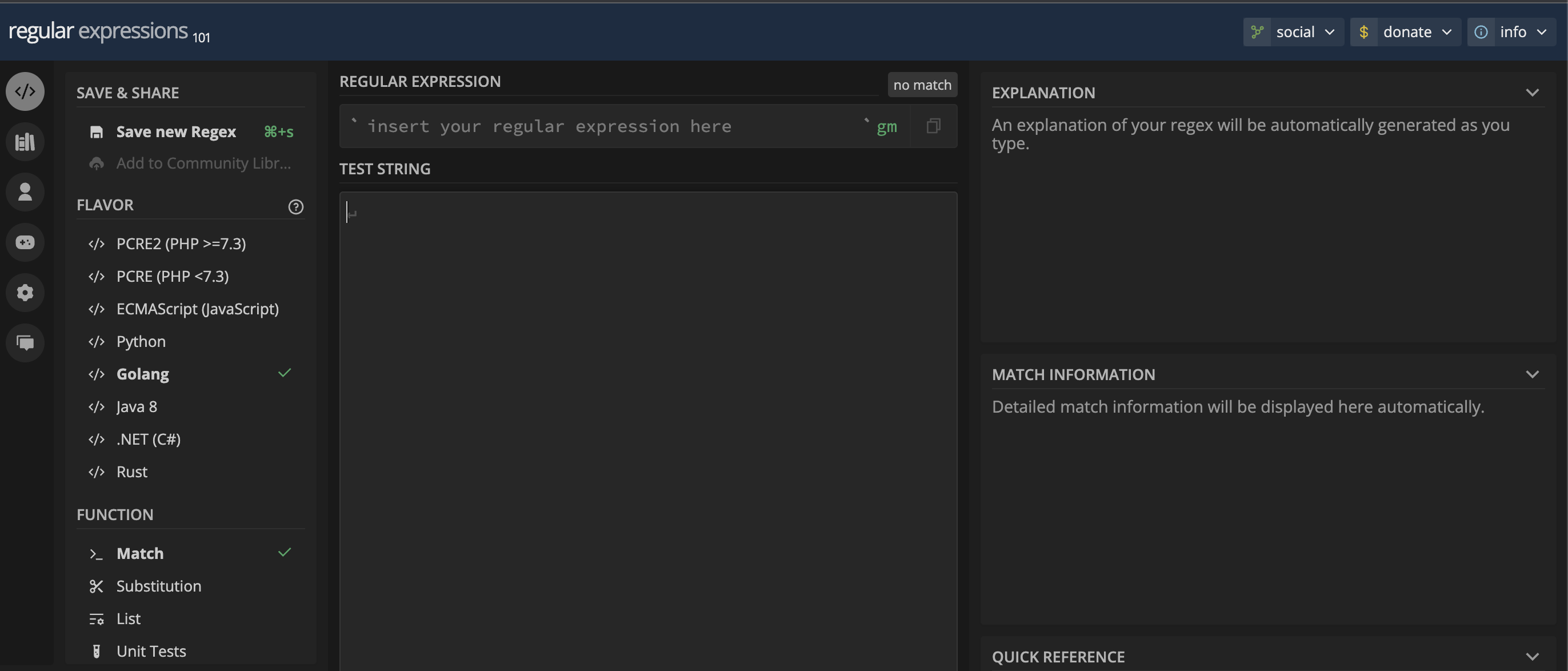
Make sure to select Golang (the regex flavor utilized by the TruffleHog scanning engine)
and confirm the gm on the right of the text field.
If not, click into it and adjust the regex flag to global multiline.
Enter in the regex pattern you’d like to detect.
Confirm in Regex101 that the regex pattern matches with the desired type of strings you’d like to detect.
The explanation panel on upper right will translate what the regex pattern specifically looks for and the quick reference panel on the bottom can help you find the regex token to define your desired regex pattern.
Verification
Verification is done via a webhook POST request to the provided
endpoint. unsafe must be
set to true if the endpoint is HTTP. Provided headers
will be sent as is to the verification server.
Payload and Response
An example payload is provided for the above configuration.
{
"hog detector": {
"adjective": ["hogs are cool", "cool"]
}
}
The first index in the array is the full match and subsequent indices are any sub-matches (delineated by surrounding parentheses in the regular expression).
A response status code of 200 OK will mark the secret
as verified. Any other response status code will mark the secret as
unverified.
An example verification server in Python can be found here.